Securing the future: Navigating the risks and benefits of private 5G

Udo Schneider of Trend Micro
Private 5G networks are all the rage. At Mobile World Congress last month, IBM and Nokia joined hands to kick off the development of a “seamless, simplified private” 5G managed service offering, while Cisco and NTT announced a collaboration to bring their private 5G services to enterprise customers in selected sectors, says Udo Schneider, IoT security evangelist, Trend Micro.
Unlike earlier technologies, private 5G networks sometimes referred to as campus networks or non-public networks (NPNs) were designed from the outset to enable efficient communication between devices. They offer numerous advantages, including high bandwidth, fast speed, low latency, enhanced privacy (due to their “on-premise” components) and greater scalability, to enable deployment scenarios where radio-based technologies simply could not be used before.
But while organisations power ahead with their 5G initiatives, they must be cautious not to repeat the hard lessons from the past 25 years. Cybersecurity should not be an afterthought for private 5G, but an integral pillar in every business models.
Unlocking new opportunities
While private 5G networks can improve the return on investment (ROI) of many existing use cases for radio technologies today, they can also unlock other uses cases that were simply not possible before.
For example, time sensitive network connectivity has traditionally been a stronghold of cable-based networks. Now, with 5G and its improved latency across all layers, many new deployments of industrial control infrastructure are seriously considering a 5G model instead. The increased cost for private 5G is easily offset by the savings in physical cabling, and you’ll gain more flexibility “for free”. The scaled up support for devices and covered area also benefits smart city developments. Instead of requiring a whole host of access technologies for different classes of devices, 5G would enable coherent connectivity across a diverse range of previously disparate devices and technologies such as smart cars, autonomous vehicles (public transport, drones), intelligent traffic systems and utilities, and more.
In healthcare, streamlined remote monitoring devices simplify processes and improve patient care. Additionally, remote operating theatres require low latency and high bandwidth, which were previously unavailable, especially in remote or crisis hit areas.
Understanding deployment models
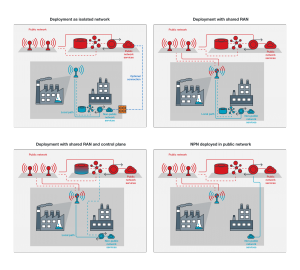
Use cases aside, there is still relatively limited awareness about how core and radio access networks function. This is because, for public mobile networks, telecom operators construct and manage both the core and radio access networks. With the emergence of private 5G, this is set to change significantly. In fact, there are several ways to run a private 5G network, including:
- Isolated network: A local network managed by the customer or by a telecom operator on their behalf.
- Shared Radio Access Network (RAN): The core network is operated locally. However, the radio access network is provided by the telecom operator and may be shared with other customers.
- Shared RAN and shared control plane: The core network is largely provided by the telecom operator. However, some domain data remains local.
- Campus Overlay Network: Also known as “Custom APN (Access Point Names), all network components come from the telecom operator and are shared. Unlike with 4G and APNs, 5G offers true network separation with network slicing.
5G security concerns
Contrary to popular belief, private 5G networks are not automatically immune to attack. Unfortunately, the secure operation of 5G equipment requires experience and technologies that are typically not available to those responsible for IT or OT combining telecoms sector knowledge (CT – Communication Technology) with their existing OT and IT knowledge. This also applies to situations where the 5G network is operated by a telecom operator, either autonomously or as a network slice.
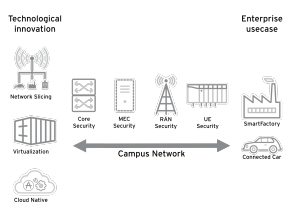
An end-to-end security approach to enterprise 5G extends from the core network to Multiaccess Edge Computing (MEC), RAN, and user experience.
Core network security: The process of virtualisation, one of the core technologies for deploying and operating 5G core networks, can make them more vulnerable to IT attacks. This is because 5G typically uses Commercial Off The Shelf (COTS) server hardware, for example, Open Compute Project (OCP) based servers and Linux software, all of which are vulnerable to IT attacks such as Spectre, Meltdown and those on BMC modules.
MEC security: MEC involves moving virtualised processing functions to the edge of the radio network, which can leave them vulnerable to traditional VM or container attacks. On the other hand, combined with applications on the SIMs (physical or eSIM), MEC solutions can ensure confidentiality and integrity of communications regardless of the mobile device.
RAN security: RAN security requires solid vulnerability management, especially for open RAN approaches, which are gaining ground for 5G deployments and rely on well-known virtualisation and operating platforms that can contain vulnerabilities.
APNs & base stations : Still often used in today’s 4G/5G networks, APNs do not provide real network separation and the use of VPNs is highly recommended5G Network slicing however does provide real separation. Meanwhile, with some core networks using cleartext or failing the check certificates well, base stations can be vulnerable to man-in-the-middle (MitM) attacks, and critical patches may require downtime planning.
User equipment: 5G user equipment, which could include autonomous industrial trucks, robots, drones, as well as regular handsets, is all prone to attacks such as SIM swapping. A SIM card can be stolen from a device and installed in the attackers to give them access to the campus network, which they can then scan for vulnerabilities, or use to attack other devices.
A new playground for cybercriminals
Per the above, the shift from traditional telecom technologies towards standards-based COTS infrastructure, combined with well-known IT technologies like virtualisation and software-defined networking all increase the attack surface of 5G networks. That said, the number of large scale attacks on private 5G environments still remains low.
However, this is not due to 5G environments being inherently more secure. From the perspective of cybercriminals, attacking 5G is currently not lucrative enough to justify the investment, particularly when compared to other approaches such as ransomware attacks on supply chains.
Nevertheless, past experiences have taught us that cybercriminals are constantly evolving their business. With 5G becoming a critical component of numerous new use cases, it is likely that cybercriminals will develop attack and business models targeting those scenarios. For customers whose entire value chain is reliant on a functioning 5G infrastructure, for example, their willingness to pay ransom will be particularly high. Therefore, it is a matter of when cybercriminals will start targeting 5G, rather than if.
Securing the network
5G networks are being used by more and more organisations to meet the demands of today’s world. However, this has significant security implications. The lines between IT, OT and CT security responsibilities are blurring, maintenance costs are rising, and IT/OT staff must equip themselves with telecoms skills to secure the network.
Secure practices and measures remain key to protecting the 5G network. Here are some that organisations can implement to strengthen their security:
- Use XDR or MDR to detect possible attacks and lateral movement within the campus network as well as within the containerised core network.
- Use VPN or IPsec to protect remote communication channels, including remote sites and base stations. LTE and 5G are not “automatically” encrypted!
- Use cybersecurity tools that understand core network protocols.
- Ensure proper network segregation with VLANs or SDN.
- Patch servers, routers, and base stations in a timely manner. As many components in the core network run on Linux, pay particular attention to signs of Linux vulnerabilities.
- Invest in anomaly detection products for the campus network which provide a good way to eliminate unlisted device/SIM card pairs.
- Understand the limitations of your vendor’s APN or network slicing solution, and deploy additional defences as needed.
The author is Udo Schneider, IoT security evangelist, Trend Micro.
Comment on this article below or via Twitter @IoTGN
