loodgate CA designed for OEMs to quickly and cost-effectively deploy a ‘private’ PKI network

Icon Labs, a provider of security solutions for IoT and edge devices, has announced the availability of the Floodgate Certificate Authority (CA).
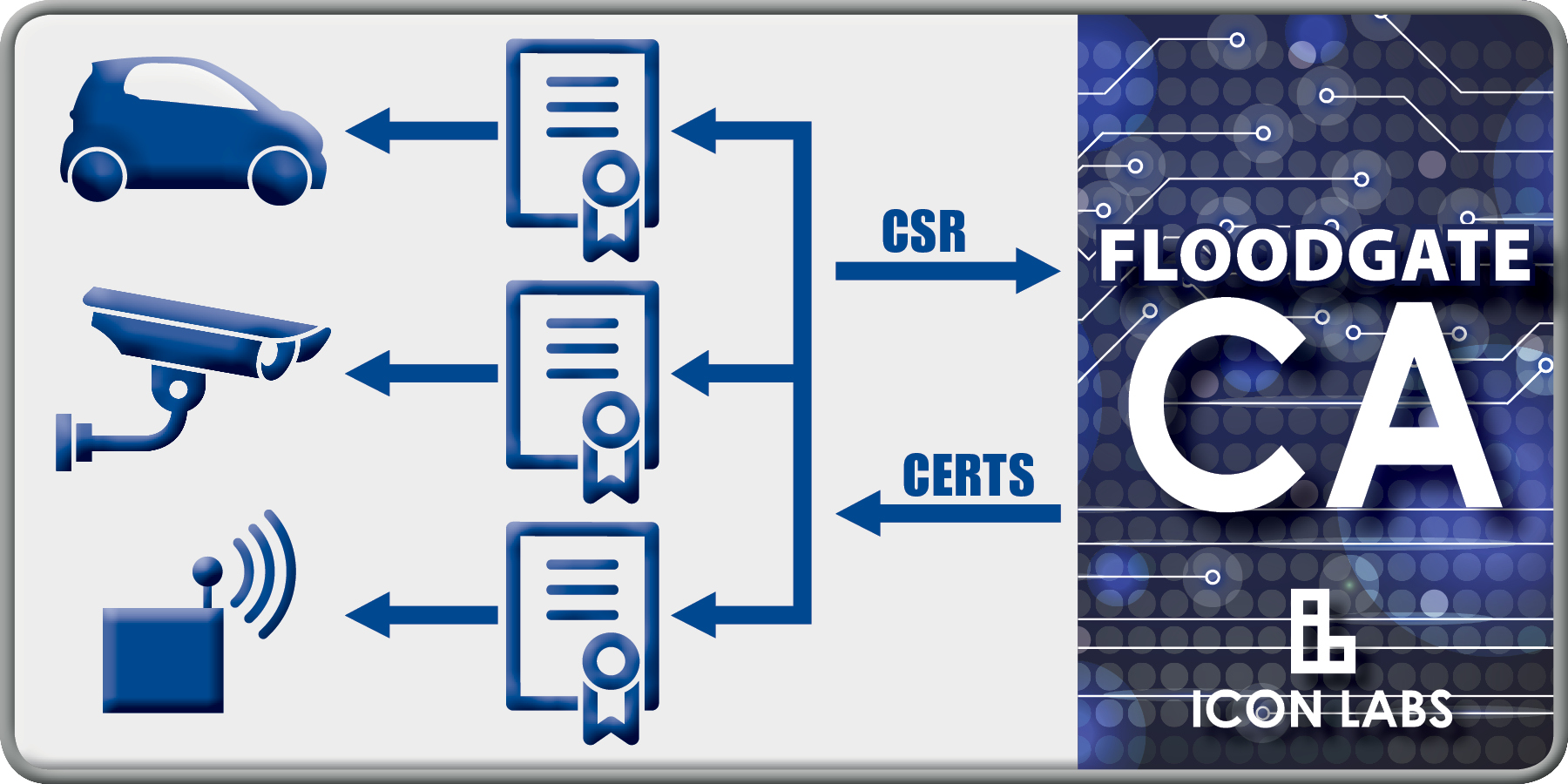
Floodgate CA is the server-side portion of Icon Labs’ PKI solution and provides certificate management for companies choosing to implement their own certificate-based authentication using public key infrastructure.
IoT security requires strong authentication. All IoT devices, including the smallest endpoints, must support mutual authentication, ensuring all communication is between known, trusted devices, and that all access is authorised. Certificate-based authentication using Public Key Infrastructure (PKI) provides a proven, reliable authentication method.
The Floodgate CA can be deployed on a hardened server or hierarchy of servers in a private environment to provide a closed PKI system without dependence upon public certificate authorities or other third-parties. It can also operate as a sub-CA of a public CA, allowing original equipment manufacturers (OEMs) to choose the operating model based on their IoT authentication requirements.
Floodgate CA can be used with any PKI client, including Icon Labs’ Floodgate PKI Client Toolkit; an embeddable PKI client for IoT devices. Floodgate PKI Client enables even the smallest of IoT devices to generate keys, create certificate signing requests, and retrieve signed certificates from the Certificate Authority.
“This is the only security solution that provides both the client and server side required to automate secure provisioning and enrollment,” said Alan Grau, president of Icon Labs. “The Floodgate Certificate Authority and Floodgate PKI Client toolkit enables developers to easily and efficiently integrate certificate-based machine-to-machine authentication for IoT devices.”
The PKI client supports SCEP, EST, and OCSP on all RTOS, embedded Linux, and Windows devices.
The Floodgate Certificate Authority encompasses a wide-range of potential use cases including key management, generating public key infrastructure certificates, and injecting pre-generated keys during the manufacturing process.
Gartner Research has said, “PKI will re-emerge as one of the most relevant authentication mechanisms for organisations addressing the IoT authentication problem.
PKI’s flexibility is important when adapting to changing requirements and represents identity verification in a cross-platform, multiprotocol approach.”
Icon Labs’ products provide embedded security for IoT and Machine-to-Machine (M2M) solutions in aerospace, industrial, medical control devices, and consumer electronics.
The Floodgate Security Framework provides a “defense in depth” solution to protect control units and endpoint devices from cyber threats, aid in compliance with regulatory mandates and guidelines, and gather and report command, event, and device status information for audit requirements.
Comment on this article below or via Twitter @IoTGN