Facing the NFV security challenge

Alex Leadbeater of ETSI
NFV will transform the way networks are run and managed, but the area also represents a major security challenge. As the authors, Igor Faynberg, chairman, and Alex Leadbeater, vice chairman, ETSI NFV Security Working Group ask, how can this be overcome?
A cyber-attack on today’s physical mobile networks can be, in the worst case, overcome by simply unplugging a cable or disabling physical hardware. But this is about to change as network functions virtualisation (NFV) based on cloud architecture enables the networks of the future.
Indeed, as mobile networks transform from physical to virtual they become much more complex to secure. While cloud and virtualisation offer flexibility and adaptability, they also widen the scope for adversaries to attack the network.
At the same time, the move to virtualisation will see networks carrying larger amounts of data than ever before, which must be adequately protected. This is further compounded by the update to general data protection regulation (GDPR) which came into force on 25th May this year, outlining increased rights for customer data, including fines for those who fail to comply.
Under the GDPR, telecoms firms are expected to be able to identify where their data is and show they have taken steps to protect sensitive information from adversaries. Part of the GDPR is ensuring security by design and default, including measures such as encryption – which makes the regulation an ideal bench-marking tool for NFV security.
It’s a complex picture, but that’s not to say NFV is less secure than legacy networks: if implemented correctly, NFV security has the potential to be even more effective than previous systems. However, if virtualised networks are not implemented well and properly safeguarded, the consequences can be devastating. It is therefore essential that they are designed to include security from the start.
Addressing security problems
It is clear that securing NFV will require a completely different approach. Yet the area also presents unique opportunities for addressing security problems. For example, NFV offers the ability to improve the security properties of network functions: It can facilitate agile provision of secure services by the carrier and provide better protection of the carrier cloud.
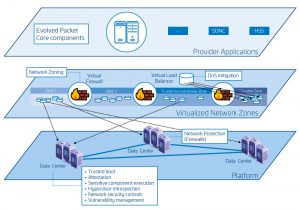
In addition, one of the major advantages of the move to NFV is the ability to offer more adaptive security. Because virtualised networks consist of software, they are able to distribute security monitoring and firewalls across the network in a more cost-effective way. This contrasts to measures such as placing firewalls in between physical functions – which can be expensive and usually requires visiting a physical location to replace assets.
NFV also offers the ability to adapt and monitor in real time across the network. So, one way of securing virtualised networks is by using automated tools to monitor for unusual activity that might indicate they are under attack. Powered by artificial intelligence (AI) and machine learning, these tools aren’t intended to replace the security analyst. Indeed, some solutions are able to detect and mitigate attacks, but most will flag issues for a security analyst to look into.
In addition to these technical tools, it is important that standards are in place to join together functions and analyse security. That is why ETSI’s security group is tasked with looking across the industry specification group (ISG) for fundamental security, at the same time examining what architecture test groups are developing in the area.
The group is also offering resources to help the industry. Last October, ETSI’s technical committee on cyber security (TC CYBER) released its TR 103 456 report offering guidance to enterprises, government agencies and services providers on how to implement the EU’s Directive on Security of Network Information Systems (NIS Directive).
The report covers sharing and exchanging information, incident notifications, technical and systems risk management, challenges and solutions and technical recommendations.
ETSI specifications
The NFV SEC Working Group (WG) comprises computer, network, and cloud security experts representing network operators, equipment vendors, and law enforcement agencies. They have been advising the NFV ISG about the relevant security technologies while developing a wide range of industry specifications.

Igor Faynberg
As part of its approach to securing NFV, the working group has produced a series of specifications including SEC012 intending to set a benchmark for sensitive workloads. Meanwhile, SEC013 covers monitoring and management, and further specifications for policy management and APIs will come later.
The aim of the specifications is to identify NFV-specific security problems as well as to examine the technological advantages of the NFV environment that can be harnessed to improve the security of network operators’ services.
It is with this ethos in mind that the group is aiming to provide specific guidance on various aspects of NFV security in a systematic, holistic manner. This will include building trust from secure hardware modules to software and covering identity management, authentication, authorisation, and secure attestation. The group will also examine a means of global monitoring for the whole NFV environment and implement decisive operational security actions in response to breaches.
The working group is looking at solutions to the problem of implementing Critical National Infrastructure (CNI) in the NFV environment, working in close collaboration with other ETSI NFV working groups, as well as wider external organisations, such as open source groups.
Taking into account the sum total of ETSI’s work in NFV security so far, it is clear a good start has been made, but there is still much work to be done. Even as new security measures are put into place, cyber criminals will always find more ways to attack and compromise the network, so it’s important to say one step ahead.
The industry agrees it is a complex area. But ETSI is continuing its work across NFV, 5G and quantum computing, with groups working closely with TC CYBER to ensure that security aspects are included in all of its specifications from the outset. For more information click here
The authors of this blog are Igor Faynberg, and Alex Leadbeater of ETSI NFV Security Working Group
Comment on this article below or via Twitter @IoTGN
